As a website owner, you know how important it is to protect your online presence from various types of attacks. One of the most effective ways to do this is by setting up HTTP Security Headers, which act as a shield against XSS, code injection, clickjacking, and other malicious activities. Without these headers, your website is vulnerable to attacks that can compromise user data and damage your reputation. In this tutorial, you will learn how to configure HTTP Security Headers on a WordPress website using the Headers Security Advanced plugin, ensuring your website is secure and protected from potential threats.
Understanding HTTP Security Headers
The primary function of HTTP Security Headers is to protect your website from various types of attacks, such as XSS, code injection, and clickjacking. These headers instruct the browser on how to display your website securely, ensuring that your users’ data remains safe.
Types of HTTP Security Headers
There are several types of HTTP Security Headers, including:
- Cross Site Scripting Protection (X-XSS)
- Content Security Policy (CSP)
- Browser Sniffing Protection (X-Content-Type-Options)
- Clickjacking Prevention (X-Frame-Options)
- HTTP Strict Transport Security (HSTS)
This list is not exhaustive, but it covers some of the most important HTTP Security Headers.
| Header Type | Description |
| X-XSS-Protection | Protects against cross-site scripting (XSS) attacks |
| Content Security Policy (CSP) | Defines which sources of content are allowed to be executed within a web page |
| X-Content-Type-Options | Prevents browser sniffing attacks |
| X-Frame-Options | Prevents clickjacking attacks |
| HTTP Strict Transport Security (HSTS) | Ensures that a website is only accessed over HTTPS |
Importance of HTTP Security Headers
To ensure the security of your website, it’s important to configure HTTP Security Headers correctly. Without these headers, your website may be vulnerable to various types of attacks, which can compromise your users’ data.
Security is a top priority when it comes to website development. By implementing HTTP Security Headers, you can significantly reduce the risk of attacks and protect your users’ sensitive information. Failing to configure these headers can lead to serious security breaches, which can damage your reputation and result in financial losses. Therefore, it’s crucial to understand the importance of HTTP Security Headers and implement them correctly.
Factors to Consider When Setting Up HTTP Security Headers
Some key factors to consider when setting up HTTP security headers include browser sniffing protection, clickjacking prevention, and cross-site scripting protection. You should also consider the specific security needs of your website and the potential risks associated with each type of attack. Assume that your website is vulnerable to attacks if you don’t configure HTTP security headers properly.
Browser Sniffing Protection
Sometimes, browsers can be tricked into interpreting files of different types, leading to security vulnerabilities. To prevent this, you can set the X-Content-Type-Options header to “nosniff”, which prevents the browser from sniffing the MIME type of a file.
Clickjacking Prevention
Factors such as allowing your website to be framed by other websites can lead to clickjacking attacks. To prevent this, you can set the X-Frame-Options header to “SAMEORIGIN”, which prevents your website from being framed by other websites.
For instance, if an attacker tries to frame your website, the browser will prevent the framing action, reducing the risk of clickjacking attacks.
Cross-Site Scripting Protection
Headers such as Content-Security-Policy and X-XSS-Protection can help prevent cross-site scripting attacks. These headers define which sources of content are allowed to be executed within a web page.
To ensure maximum protection, you should set the X-XSS-Protection header to “1; mode=block”, which enables XSS filtering and sets the blocking mode. Additionally, you can set the Content-Security-Policy header to define the allowed sources of content.
Tools for Checking HTTP Security Headers
● Check HTTP Security Headers: www.securityheaders.com
● Check WebPageTest: www.webpagetest.org
● Check HSTS test website: https://gf.dev/hsts-test
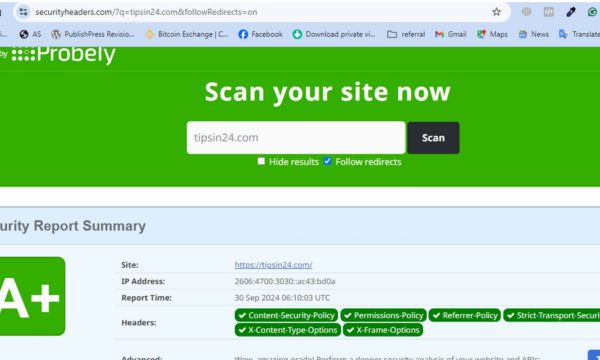
The tools allow you to evaluate your HTTP Strict Transport Security (HSTS) implementation and overall header security status. By regularly assessing your headers, you safeguard against vulnerabilities such as cross-site scripting and clickjacking, ensuring a safer experience for your users. Engaging these tools is a step toward fortifying your website’s defenses.
Using the Headers Security Advanced Plugin
Headers Security Advanced Plugin:
https://wordpress.org/plugins/headers-security-advanced-hsts-wp/
WordPress Dashboard > Settings > Headers Security Advanced & HSTS WP
One of the easiest ways to configure HTTP security headers on your WordPress website is by using the Headers Security Advanced plugin. This plugin provides a range of features, including:
- HSA Limit Login to block brute force attacks
- X-XSS-Protection
- Expect-CT
- Access-Control-Allow-Origin
- And many more
| Plugin Feature | Description |
|---|---|
| HSA Limit Login | Blocks brute force attacks |
| X-XSS-Protection | Protects against cross-site scripting (XSS) attacks |
Manual Configuration HTTP Security Headers using.htaccess
If you prefer not to use a plugin, you can manually configure HTTP security headers by adding the following codes to root.htaccess file:
# BEGIN Headers Security
<IfModule mod_headers.c>
Header set Access-Control-Allow-Methods “GET,POST”
Header set Access-Control-Allow-Headers “Content-Type, Authorization”
Header set Content-Security-Policy “upgrade-insecure-requests;”
Header set Cross-Origin-Embedder-Policy “unsafe-none; report-to=’default'”
Header set Cross-Origin-Embedder-Policy-Report-Only “unsafe-none; report-to=’default'”
Header set Cross-Origin-Opener-Policy “unsafe-none”
Header set Cross-Origin-Opener-Policy-Report-Only “unsafe-none; report-to=’default'”
Header set Cross-Origin-Resource-Policy “cross-origin”
Header set Permissions-Policy “accelerometer=(), autoplay=(), camera=(), cross-origin-isolated=(), display-capture=(self), encrypted-media=(), fullscreen=*, geolocation=(self), gyroscope=(), keyboard-map=(), magnetometer=(), microphone=(), midi=(), payment=*, picture-in-picture=(), publickey-credentials-get=(), screen-wake-lock=(), sync-xhr=(), usb=(), xr-spatial-tracking=(), gamepad=(), serial=()”
Header set Referrer-Policy “strict-origin-when-cross-origin”
Header set Strict-Transport-Security “max-age=63072000”
Header set X-Content-Security-Policy “default-src ‘self’; img-src *; media-src * data:;”
Header set X-Content-Type-Options “nosniff”
Header set X-Frame-Options “SAMEORIGIN”
Header set X-XSS-Protection “1; mode=block”
Header set X-Permitted-Cross-Domain-Policies “none”
</IfModule>
# END Headers Security
Advanced users can manually configure HTTP security headers by adding the following codes to their.htaccess file. This method requires a good understanding of.htaccess files and may not be suitable for beginners.
Important: Make sure to backup your.htaccess file before making any changes.
Pros and Cons of HTTP Security Headers
After setting up HTTP security headers, it’s necessary to understand their benefits and limitations. This will help you make informed decisions about implementing these headers on your website.
| Pros | Cons |
|---|---|
| Enhanced security against XSS, code injection, and clickjacking attacks | May require additional configuration and testing |
| Improved protection against protocol downgrade attacks and cookie hijacking | Some headers may not be compatible with older browsers |
| Increased trust and credibility with users and search engines | May require additional resources and expertise to implement |
| Better compliance with security standards and regulations | Some headers may have performance implications |
| Enhanced control over content and resource loading | May require additional maintenance and updates |
Join Our Telegram Group
Benefits of Implementing HTTP Security Headers
An necessary aspect of website security, HTTP security headers provide a robust defense against various types of attacks. By implementing these headers, you can significantly reduce the risk of security breaches and protect your users’ sensitive information.
FAQ
Q: What are HTTP Security Headers, and how do they enhance website security?
A: HTTP Security Headers are a set of response headers sent by a web server to a client’s browser that instruct the browser on how to process and secure the content of a web page. These headers play a significant role in protecting websites from various attacks, including Cross-Site Scripting (XSS), code injection, and clickjacking. By implementing these security headers, websites can define policies that restrict malicious content execution, ensure secure connections, and limit how their data can be shared or accessed across different origins.
Q: What are some common types of HTTP Security Headers and their functions?
A: There are several important HTTP Security Headers that serve different purposes to safeguard a website:
- X-XSS-Protection: This header enables or disables the cross-site scripting filter built into most browsers. If set to “1; mode=block”, it will block the page from loading if an attack is detected.
- Content-Security-Policy (CSP): CSP defines a whitelist of sources from which resources can be loaded, helping to prevent XSS and related attacks.
- X-Frame-Options: This header prevents clickjacking by restricting how the web page can be displayed in frames or iframes.
- Strict-Transport-Security (HSTS): HSTS enforces secure (HTTPS) connections to a website, mitigating the risk of man-in-the-middle attacks.
- Referrer-Policy: This header controls the amount of information that is passed along when navigating from the website or making requests from it, thereby enhancing privacy.
Q: How can website owners configure HTTP Security Headers effectively?
A: Website owners can configure HTTP Security Headers effectively by using plugins or by modifying server configurations directly. For WordPress sites, a popular choice is the Headers Security Advanced plugin, which provides an easy interface for setting up these headers without needing to directly edit code. Alternatively, webmasters may incorporate header settings directly into the server’s .htaccess file. It is advisable to check the effectiveness of the configured headers using online tools like securityheaders.com to ensure that all intended protections are properly implemented.
Summing up
Upon reflecting on the steps outlined in this tutorial, you should now have a comprehensive understanding of how to set up HTTP security headers for maximum protection on your WordPress website. By following the instructions and configuring the Headers Security Advanced plugin, you’ve taken a significant step in safeguarding your website against various types of attacks, including XSS, code injection, and clickjacking. Your website is now more secure, and you can rest assured that your users’ data is better protected.